Individual behavior towards Cyber security
Introduction
At present, the need of cyber security is essential as today’s culture has evolved into a true cyber society, with people relying on information and communication technology in their daily lives. [1]. In today’s fast-paced society, mobile technologies in the information era have the capability and advanced features of computers and communication. Technology has become central and commonplace in everyone’s lives without their knowledge, and users are vulnerable to cyber-attacks. Since the massive progress and growth of the information technology industry has increased the technical needs in organisations and among their people, information security is seen as a concern in organisations and industries. However, the reason for handling information security has proven to be a key concern for many organizations as issues related to security are prevalent due to easy access of information [2]. When information securing technologies have struggled to secure organisations from cyber-attacks, the human factor of information security has been demonstrated in particular and its impact in cyber security is a existing concern as indicated [3] and also human behaviour is presented as a risk factor [4].

Survey on cybersecurity
Although there are extensive literatures on information security, most of the security researches have focused on the technical aspects of information management systems, neglecting the human behaviour factor. The human element is also under constant attack, despite the accelerated growth and deployment of new technical technologies to address the increasing challenge to information security. As a result, in order to create a comprehensive and statistical model that can determine cyber security risks, human behaviour factors must be highlighted in order to perceive the effect of customer, sponsor, and perpetrator activities on cyber security [5].
According to many international reports [6], [7], most of the advanced cyber-attacks are frequently built on human vulnerabilities mainly human behaviour and hence role of humans cannot be ignored in a successful cyber security strategy. However, human behaviour is inconsistent, according to research, and may be heavily motivated by relationships; there is also a widespread conviction that negative things only happen to other people. Risky behaviour is also linked to the human actions of cyber security, where individuals would engage in an operation despite the fact that there was a known risk involved. Therefore, Organizations must use behavioural experts to analyse data security activities from cognitive and bias perspectives and also should consider other behavioural aspects, in order to create an integrated approach to capitalised technologies, systems, and procedures to optimise security [8], [9]. Theoretical models of the factors that influence an individual’s behaviour towards security are shown below
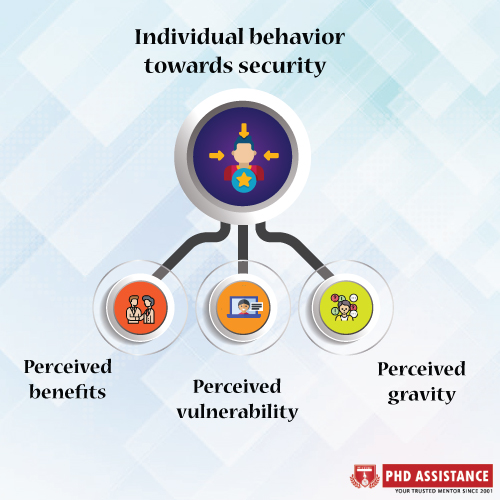
Figure 1: Individual attitude towards security
Perceived vulnerability: It symbolizes a person’s perception that he or she has been harmed in a way that may lead to an online assault.
Perceived gravity: It reflects a person’s reaction to the effects of a computer crash.
Perceived benefits: It refers to the advantages that people see in embracing safety attitudes.
Conclusion
The battle against cybercrime and the avoidance of digital threats inside companies shifts the focus from technology to the human factors; The Research on Individual behavior towards cyber security will become increasingly relevant. Thus, analyzing individual behavior towards cyber security can support organizations in their information security processes. If a more comprehensive paradigm of how people want to participate in successful cyber security practices is built, tactics to spread these practices further have the potential to emerge.
References
[1] H. de Bruijn and M. Janssen, “Building Cybersecurity Awareness: The need for evidence-based framing strategies,” Gov. Inf. Q., vol. 34, no. 1, pp. 1–7, Jan. 2017, doi: 10.1016/j.giq.2017.02.007.
[2] E. Kolkowska, F. Karlsson, and K. Hedström, “Towards analysing the rationale of information security non-compliance: Devising a Value-Based Compliance analysis method,” J. Strateg. Inf. Syst., vol. 26, no. 1, pp. 39–57, Mar. 2017, doi: 10.1016/j.jsis.2016.08.005.
[3] M. Evans, L. A. Maglaras, Y. He, and H. Janicke, “Human behaviour as an aspect of cybersecurity assurance,” Secur. Commun. Networks, vol. 9, no. 17, pp. 4667–4679, 2016, [Online]. Available: https://onlinelibrary.wiley.com/doi/abs/10.1002/sec.1657.
[4] M. Anwar, W. He, I. Ash, X. Yuan, L. Li, and L. Xu, “Gender difference and employees’ cybersecurity behaviors,” Comput. Human Behav., vol. 69, pp. 437–443, Apr. 2017, doi: 10.1016/j.chb.2016.12.040.
[5] D. Henshel, M. G. Cains, B. Hoffman, and T. Kelley, “Trust as a human factor in holistic cyber security risk assessment,” Procedia Manuf., vol. 3, pp. 1117–1124, 2015, [Online]. Available: https://www.sciencedirect.com/science/article/pii/S2351978915001870.
[6] Verizon, “Data Breach Investigations Report,” 2017. https://www.verizon.com/business/resources/reports/dbir/.
[7] Pwc, “The Global State of Information Security® Survey,” 2018, [Online]. Available: https://www.pwc.com/us/en/services/consulting/cybersecurity-privacy-forensics.html.
[8] S. L. Pfleeger and D. D. Caputo, “Leveraging behavioral science to mitigate cyber security risk,” Comput. Secur., vol. 31, no. 4, pp. 597–611, Jun. 2012, doi: 10.1016/j.cose.2011.12.010.
[9] N. S. Safa, M. Sookhak, R. Von Solms, S. Furnell, N. A. Ghani, and T. Herawan, “Information security conscious care behaviour formation in organizations,” Comput. Secur., vol. 53, pp. 65–78, Sep. 2015, doi: 10.1016/j.cose.2015.05.012.



